CEH v11 module3 – Scanning Networks
3 10 月, 2022
/
0x01 Networking
- Check for live systems
- Check for open ports
- Discover operating system
- Discover system architecture
- Discover service
- dicover vulnerabilities
0x02 - TCP Communication Flags
0x02 - A TCP flag
- SYN
- 必要的flag
- 通知傳輸一個新的序列號
- 該標誌一般代表兩台主機之間建立連接
- ACK
- 必要的flag
- 確認接收到傳輸並識別下一個預期的序列號。
- 當系統成功接收到一個數據包時,它會將其標誌的值設置為“1”,從而暗示接收者應該注意它。
- PSH (插隊用)
- 當設置為“1”時,表示發送方已經向接收方發起了推送操作;這意味著遠程系統應通知接收應用程序有關來自發送方的緩衝數據。
- 系統在數據傳輸的開始和結束時產生 PSH 標誌,並將其設置在文件的最後一段以防止緩衝區死鎖。
- URG (插隊用)
- 它指示系統盡快處理數據包中包含的數據。
- 當系統將該標誌設置為“1”時,優先處理緊急數據,並停止所有其他數據處理。
- FIN
- 必要的flag
- 設置為“1”表示不再向遠程系統發送傳輸,並且由 SYN 標誌建立的連接終止。
- RST
- 必要的flag
- 前連接出現錯誤時,該標誌設置為“1”,連接被中止以響應錯誤。
0x02 - B TCP Communication
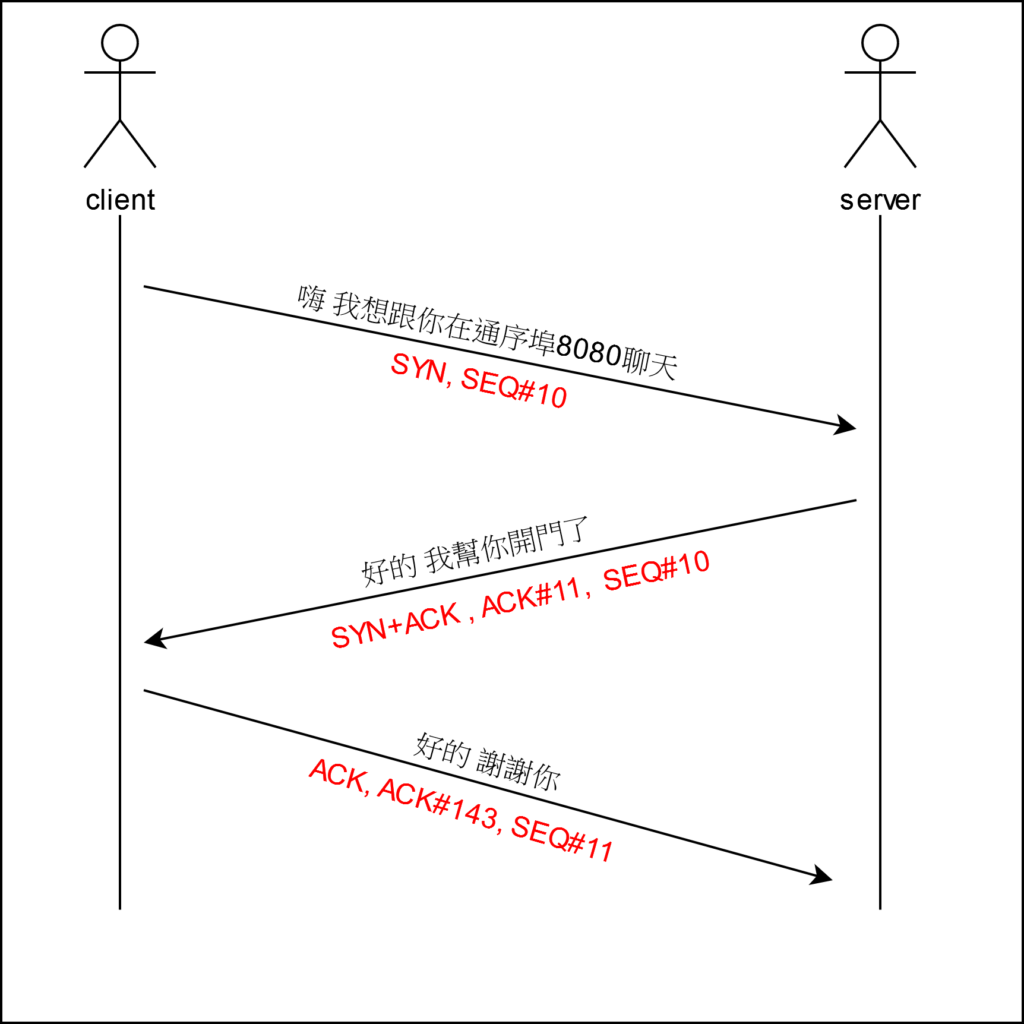
- 開始傳送
- 首先,client先向server發送一個SYN
- server收到SYN後要回復一個SYN+ACK回去
- client就會在發送一個ACK過去就表示開始通信傳輸了
- 檔案傳輸完畢(需通知結束)
- 首先client先向server端方送一個FIN
- server收到後回覆一個ACK過去表示收到FIN
- server立刻在回覆一個FIN告訴client我也準備好結束了
- client再回復一個ACK表示收到 這樣就完成雙方斷線流程
0x03- Important ICMP codes
- 0: Echo Reply
- Answer to a Type 8 Echo Request
- 3
- Destination Unreachable
- 5 Redirect
- Sent when there are two or more gateways available for the sender to use. Followed by these codes:
- 0 – Redirect datagram for the network
- 1 – Redirect datagram for the host
- Sent when there are two or more gateways available for the sender to use. Followed by these codes:
- 8
- Echo Request
- 11
- Time Exceeded
0x04- hping
- — flooding 瘋狂發送封包(洪水攻擊)
-a假來源-ccount-FFIN scan-PPUSH scan-UURG scan--rand-destrandom destionation address mode-I <interface>network interface namehping3 -s 192.168.1.1 -a 192.168.1.254 -p 22 --flood-1Sets ICMP mode-2Sets UDP mode-8Sets scan mode. Expects port range without -p flag-9Listen mode. Expects signature (e.g. HTTP) and interface (-I eth0)
–flood Sends packets as fast as possible without showing incoming replies-QCollects sequence numbers generated by the host-pSets port number-FSets the FIN flag-SSets the SYN flag-RSets the RST flag-PSets the PSH flag-ASets the ACK flag-USets the URG flag-XSets the XMAS scan flags
0x05- nmap
0x05 - A nmap 指令
-sn確認是否存在設備-PEping scan-PRARP scan-PUUDP Ping Scan-sAACK scan-sFFIN scan-sIIDLE scan-sLDNS scan (list scan)-sNNULL scan-sOProtocol scan (tests which IP protocols respond)-sPor-snPing scan-sRRPC scan-sSSYN scan-sTTCP connect scan-sWWindow scan-sXXMAS scan-AOS detection, version detection, script scanning and traceroute-sVDetermine only service/version info-PIICMP ping-PnNo ping-PoNo ping-PSSYN ping-PTTCP ping-oNNormal output-oXXML output-nNever do DNS resolution/Always resolve-f–mtu : fragment packets (optionally w/given MTU)-DIP address Decoy: <decoy1,decoy2[,ME],…>: Cloak a scan with decoys-FFast mode – Scan fewer ports than the default scan
0x05 - B Stealth Scan
- only SYN packets sent. Responses same as full.
- Half-open scan
- SYN scan
- Useful for hiding efforts and evading firewalls
指令: nmap -sS <target IP>
0x05 - C Full connect
- Full connection and then tears down with RST.
- Easiest to detect, but most reliable (易被發現,但結果最可靠)
指令 : nmap -sT <target IP>
0x05 - D TCP ACK scan / flag probe - multiple methods
- TTL version – if TTL of RST packet < 64, port is open
- Window version – if the Window on the RST packet is anything other than 0, port open
- Window version – if the Window on the RST packet is anything other than 0, port open (確認是否有防火牆)
- 指令 :
nmap -sA <target IP>(ACK scan) - 指令 :
nmap -sW <target IP>(Window scan)
0x05 - E NULL, FIN and Xmas Scan
- 可以繞過無狀態防火牆
- Open gives no response. Closed gives RST/ACK
- 指令 :
nmap -sN <target IP>(Null scan) - 指令:
nmap -sF <target IP>(FIN scan)
- 指令 :
- Xmas Scan
- Sets the FIN, PSH, and URG flags, lighting the packet up like a Christmas tree.
- Responses are same as Inverse TCP scan
- Do not work against Windows machines
- 指令 :
nmap -sX <target IP>
0x05 - F IDLE Scan
- uses a third party to check if a port is open
- 指令 :
nmap -sI <zombie host> <target IP>
- 指令 :
0x05 - G Spoofing
- Decoy:
- 指令 :
nmap -Pn -D <spoofed IP> <target> - This will perform a spoofed ping scan.
- 指令 :
- Source Address Spoofing:
- 指令 :
nmap -e <network interface> -S <IP source> <target> - 指令 :
nmap -e eth0 -S 10.0.0.140 10.0.0.165
- 指令 :
- MAC Address Spoofing:
- 指令 :
nmap --spoof-mac <MAC|Vendor> <target> Example --> nmap --spoof-mac Cis 10.0.0.140
- 指令 :
0x05 - H Firewall Evasion
- Multiple Decoy IP addresses
- 指令 :
nmap -D RND:<number> <target> - 指令 :
nmap -D RND:10 192.168.62.4
- 指令 :
- IP Fragmentation (封包切割)
- 指令 :
nmap -f <target>
- 指令 :
- Maximum Transmission Unit
- This command is used to transmit smaller packets instead of sending one complete packet at a time.
- 指令 :
nmap -mtu 8 <target>- Maximum Transmission Unit (-mtu) and 8 bytes of packets.
0x05 - I Timing & Performance
- 指令 :
nmap <target> -T0- 1~5
- 3 預設
- 5 快速
- 1 超詳細
0x06 ProxyChains
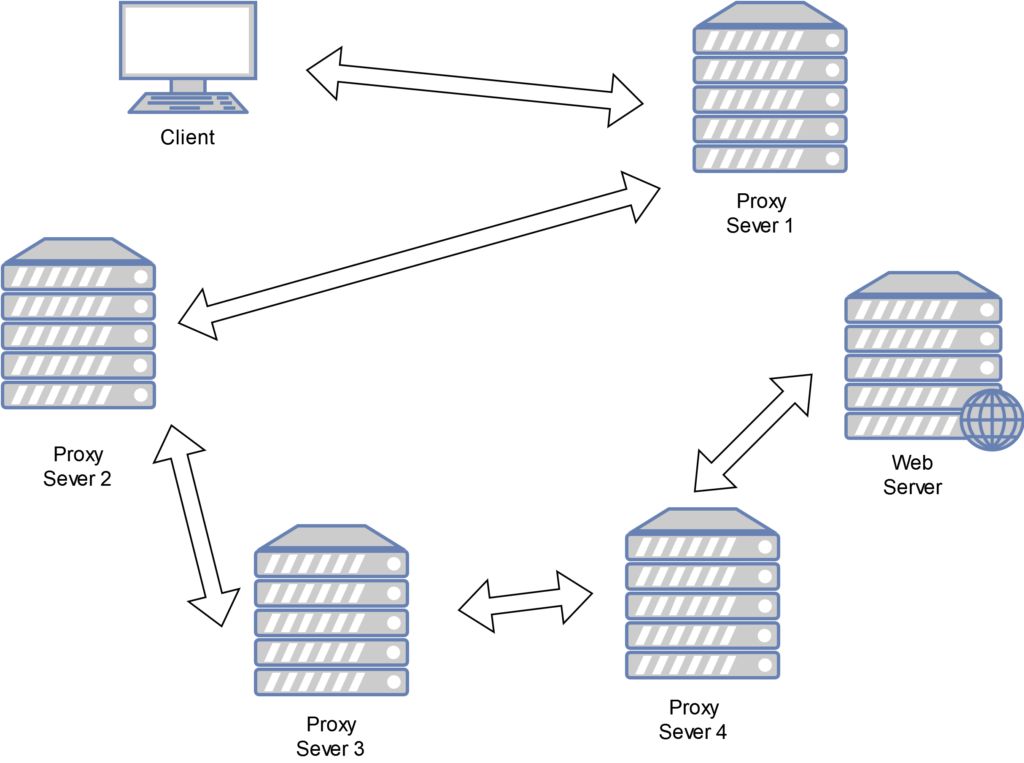
- Support SOCKS5, SOCKS4, and HTTP/HTTPS CONNECT proxy servers.
- 代理上網
- 相關工具
- Proxy Switcher
- GyberGhost VPN
- Burpsuit
- Tor
0x07 - scanning tool
- Metasploit
- NetScanTools Pro
- Unicornscan
- SolarWinds Port Scaaner
- PRTG Network Monitor
- OmniPeel Network Protocol Analyzer (無線網路)